Decentralized Storage Security Checker
Security Features Checklist
End-to-End Encryption
EssentialData is encrypted before leaving your device.
Redundant Distribution
CriticalData is stored across multiple nodes for resilience.
User-Controlled Keys
EssentialYou control the encryption keys, not the service provider.
Consensus & Proofs
AdvancedNetwork verifies data integrity through proofs.
Blockchain Transparency
OptionalStorage contracts logged on a blockchain for verification.
DDoS Resistance
CriticalNo single point of failure due to distributed nature.
Security Evaluation Results
Platform:
Data Sensitivity:
Security Score:
Overall Rating:
Recommendation:
Security Strengths:
Potential Risks:
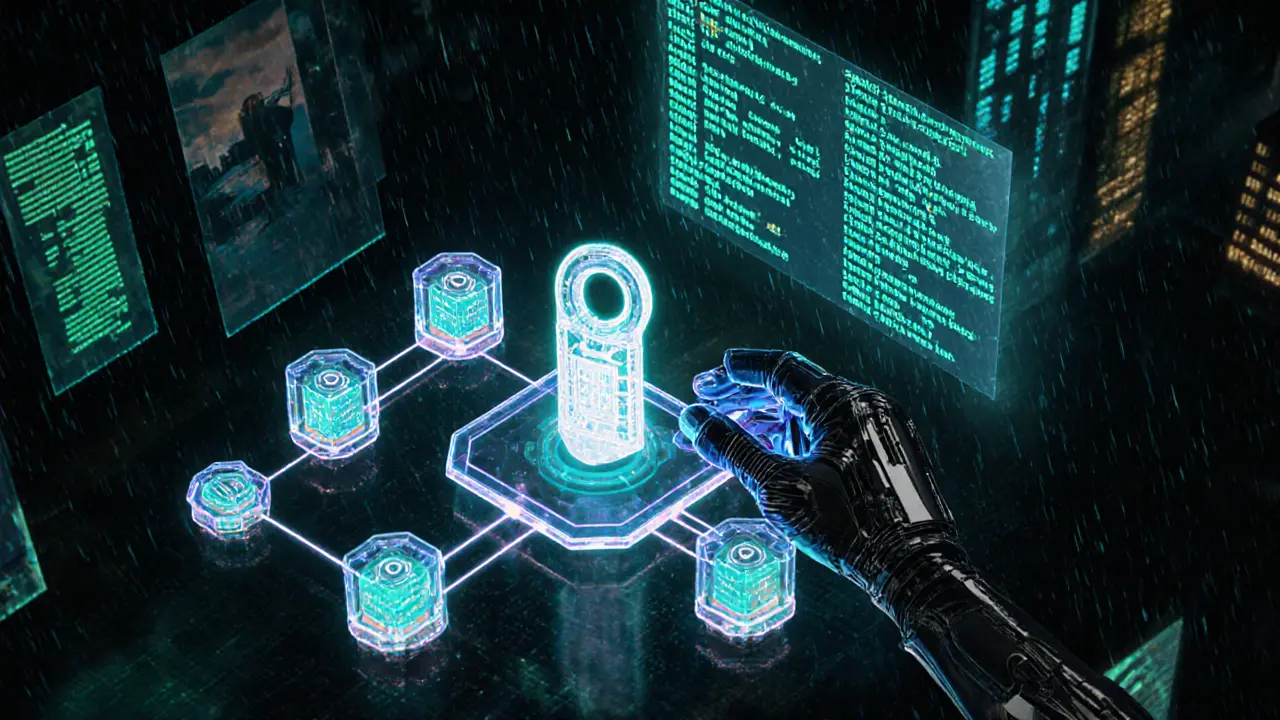
Ever worried that a single server crash could wipe out your critical files? Traditional cloud services keep your data on a handful of datacenters, meaning a breach, outage, or even a natural disaster can jeopardize everything. decentralized storage flips that model upside‑down by scattering encrypted pieces of your data across a global mesh of independent nodes. The result? A system that stays online even when parts of it go offline, and that makes it far harder for hackers to get a complete picture of your information.
Key Takeaways
- Data is split into encrypted fragments and stored on many independent nodes.
- Security relies on client‑side encryption and user‑controlled keys, not on a central authority.
- Distributed architecture naturally mitigates DDoS attacks and single‑point failures.
- Platforms like IPFS and Filecoin illustrate how the model works in real deployments.
- Successful adoption demands solid key‑management practices and understanding of network health.
What Is Decentralized Storage?
Decentralized Storage is a data‑preservation approach that distributes encrypted file fragments across a peer‑to‑peer network, eliminating reliance on a single, centrally‑controlled server farm. Instead of uploading a whole document to one provider, your file is broken into dozens or hundreds of small pieces, each encrypted with a unique key, and then scattered across computers worldwide. This architecture removes the traditional "single point of failure" that plagues conventional cloud services.
How the Security Architecture Works
The strength of decentralized storage stems from several layers that protect data against different threats.
- Cryptographic Fragmentation: Before anything leaves your device, the file is sliced into shards. Each shard is individually encrypted using End‑to‑End Encryption (a method where encryption and decryption happen only on the client side, ensuring that no intermediate node can read the raw data). Even if a node is compromised, the attacker sees only random noise.
- Redundant Distribution: Shards are replicated across multiple nodes based on a configurable redundancy factor (often 3× or 5×). If one node disappears, the system can reconstruct the missing pieces from the remaining copies.
- Consensus and Proofs: Networks employ Consensus Algorithms (protocols like Proof‑of‑Storage or Proof‑of‑Replication that verify nodes are actually holding the data they claim) to guarantee integrity. Periodic audits generate cryptographic proofs that the shard remains intact.
- User‑Controlled Keys: Your private decryption keys never leave your control. This User‑Controlled Encryption Keys (keys that the data owner generates, stores, and backs up independently of the storage network) give you the final say on who can reassemble the file.
- Blockchain Transparency: Many platforms log storage contracts and proofs on a Blockchain (an immutable, distributed ledger that records transactions and can be used to verify storage agreements without a central party). This adds an audit trail and makes censorship practically impossible.
Why It Beats Centralized Cloud Storage
Centralized services like Google Drive store your data in a few massive datacenters. If those datacenters go down, or if a hacker exploits a vulnerability, all the hosted files become exposed or unavailable. Decentralized storage changes the game in three key ways:
- DDoS Resistance: A Distributed Denial‑of‑Service attack targets a single IP address or server. In a peer‑to‑peer network, there is no single address to overwhelm, so the service stays reachable.
- Enhanced Privacy: Because encryption keys are owned by the user, the storage provider cannot read or sell your data, satisfying privacy‑first regulations like GDPR.
- Resilience to Physical Disasters: Files survive earthquakes, power outages, or regional internet cuts, as copies exist on nodes in diverse geographic locations.
That said, security isn’t automatic. The robustness of any given network depends on its implementation, redundancy settings, and the diligence of its users.
Real‑World Platforms
Several projects have turned the theory into practice. Below are the most widely referenced solutions.
IPFS (the InterPlanetary File System, a protocol that creates a content‑addressable, peer‑to‑peer hypermedia distribution network) focuses on content addressing rather than location. Files are identified by a cryptographic hash; the network retrieves shards from any node holding a matching piece.
Filecoin (a blockchain‑based incentive layer built on top of IPFS that rewards miners for storing data and provides verifiable proofs of storage) adds a market mechanism. Users pay FIL tokens to contract storage, and miners earn rewards by proving they still hold the data after a set period.
Other notable entrants include Storj (using erasure coding and a cloud‑native approach) and Arweave (offering permanent, pay‑once storage). All share the core principles of fragmentation, encryption, and distributed redundancy.
Implementing Decentralized Storage Securely
Switching from a familiar cloud UI to a decentralized network can feel like moving from a car with an automatic transmission to a manual one. Here’s a practical checklist to keep your data safe:
- Generate Strong Keys: Use a reputable wallet or key‑generation tool that supports 256‑bit entropy. Store the seed phrase offline (paper, hardware wallet) and never share it.
- Backup Keys Regularly: Treat your key backup like a priceless document. Keep multiple copies in separate physical locations to survive fire or theft.
- Choose Reputable Providers: Look for platforms with audited cryptographic proofs, transparent consensus mechanisms, and active community support.
- Set Adequate Redundancy: Most clients let you define how many copies of each shard to keep. For mission‑critical data, aim for at least three replicas across distinct geographic regions.
- Monitor Node Health: Use built‑in dashboards or third‑party monitoring tools to ensure the nodes storing your shards stay online. Replace under‑performing nodes when needed.
- Test Restoration: Periodically retrieve a random file and verify its integrity. This proves your keys work and the network still holds the fragments.
Following these steps reduces the chance of an accidental lockout-something that can happen if you lose your private key.
Common Challenges and How to Overcome Them
While the security benefits are clear, users often hit a few roadblocks early on.
- Key Management Complexity: Unlike a username‑password duo, keys are large, random strings. Solution: use hardware wallets or password‑manager integrations that can store and autofill your seed phrase securely.
- Higher Initial Costs: Paying for storage tokens or deposits can feel pricey compared to a free tier on a traditional cloud. Solution: start with a small data set, monitor usage, and scale as you prove ROI.
- Learning Curve: Concepts like erasure coding, proof‑of‑replication, and content addressing are new to many. Solution: rely on provider documentation, community forums, and step‑by‑step tutorials before attempting large migrations.
- Variable Support Quality: Some platforms lack 24/7 customer service. Solution: join Discord or Telegram groups where developers and early adopters share troubleshooting tips.
Future Outlook
Industry analysts expect decentralized storage to move from niche to mainstream within the next five years. Two trends are driving that shift:
- Advanced Cryptography: New schemes like threshold signatures and homomorphic encryption will let multiple parties jointly manage keys without exposing the full secret.
- User‑Friendly Interfaces: Wallet‑style apps are getting sleek, offering one‑click key backups and drag‑and‑drop file uploads, lowering the barrier for non‑technical users.
Regulatory pressure also plays a role. As GDPR‑style laws demand that data owners retain control over their information, decentralized architectures provide a compliant path forward. Enterprises handling sensitive intellectual property, medical records, or financial data are piloting these networks to reduce risk and avoid vendor lock‑in.
Frequently Asked Questions
Is decentralized storage slower than traditional cloud services?
Speed depends on the network’s node density and your proximity to active peers. Initial upload may take longer because of fragmentation and encryption, but retrieval often matches or exceeds cloud speeds when multiple nodes serve the same shard simultaneously.
What happens if I lose my encryption key?
Without the key, the data remains encrypted and unrecoverable. That’s why key backup is the single most critical practice in decentralized storage.
Can I store large files, like video archives?
Yes. Platforms such as Filecoin are designed for petabyte‑scale storage. They split large files into many shards, each stored on different nodes, allowing you to upload multi‑gigabyte assets without a single point of failure.
Do I need to run my own node to use decentralized storage?
No. Most services let you act as a client, handling encryption and shard management locally while the network runs its own set of storage nodes. Running a node is optional and often done by participants who want to earn tokens.
Is my data truly private if it lives on a public network?
Yes, as long as you keep your private keys secret. Each shard is encrypted before it touches the network, and only you hold the keys that can recombine and decrypt the data.








Comments
23 Comments
Tilly Fluf
I appreciate the thorough overview of decentralized storage. The emphasis on encryption and redundancy really highlights the practical benefits for everyday users.
Darren R.
Oh, the moral imperative to abandon centralized clouds-how utterly revolutionary!; Yet we must also scrutinize the environmental impact of countless nodes, lest we trade one form of risk for another.
Hardik Kanzariya
Great job breaking down the concepts! If anyone feels overwhelmed, just remember: the encryption happens on your device, and the network takes care of the rest-simple as that.
Millsaps Delaine
Decentralized storage represents a paradigm shift that touches on both technical architecture and philosophical notions of data sovereignty.
By fragmenting files into encrypted shards, the system ensures that no single actor can reconstruct the whole without the proper keys.
This cryptographic dispersion is complemented by redundancy, which typically stores three or more copies across geographically diverse nodes.
Such redundancy not only guarantees availability during outages but also provides a natural defense against malicious takedowns.
The reliance on client‑side encryption places trust back into the hands of the user, aligning with contemporary privacy regulations.
Proof‑of‑Storage mechanisms, like those employed by Filecoin, create verifiable attestations that the data still resides where it should.
These proofs are periodically audited, producing a mathematically sound guarantee of integrity that surpasses traditional checksum methods.
Moreover, the integration of blockchain logging adds an immutable audit trail, making it difficult for any party to deny the existence of storage contracts.
From a performance perspective, parallel retrieval from multiple peers can actually accelerate download times compared to a single server bottleneck.
However, the initial latency may increase during upload, as each shard must be encrypted, signed, and dispatched to the network.
Users must also grapple with key management; losing the private key is equivalent to losing the data forever.
Best practices therefore include hardware wallet storage, seed phrase backups, and periodic key rotation.
The ecosystem continues to mature, with platforms like Storj offering user‑friendly interfaces that abstract much of the complexity.
As adoption grows, we can anticipate more robust SLA‑like guarantees and enterprise‑grade tooling.
Ultimately, decentralized storage aligns with the broader movement toward distributed trust and resilience on the internet.
Embracing this technology now positions individuals and organizations to safeguard their most critical assets against future central points of failure.
Jack Fans
If you’re looking for a quick start, the Storj UI is pretty intuitive-just drag, drop, and let the client handle the encryption, though you’ll want to double‑check that your recovery phrase is stored offline.
mark gray
Keep the keys safe and you’ll be fine.
Mark Briggs
Sure, it’s 'decentralized'-just another buzzword.
mannu kumar rajpoot
What if the nodes are secretly colluding? The whole model assumes honest participants, but any covert network could undermine the encryption guarantees without us even knowing.
Shanthan Jogavajjala
From an architectural standpoint, the erasure coding schema provides both fault tolerance and bandwidth efficiency, albeit at the cost of added computational overhead during encoding.
Cindy Hernandez
Remember that the synergy between encryption and redundancy is what truly secures your data; without both, you’re vulnerable on either the confidentiality or availability front.
Samuel Wilson
Your point about environmental impact is well‑taken; many projects are now exploring proof‑of‑capacity to reduce energy consumption while maintaining security.
Emily Pelton
While the theory sounds solid, in practice you still need to monitor node health-otherwise you might lose redundancy and compromise data integrity.
victor white
One could argue that the UI aesthetics mask underlying complexities; nevertheless, the underlying cryptographic guarantees remain unchanged.
Rae Harris
Jargon aside, the takeaway is simple: more copies across diverse locations means higher resilience, even if the explanation feels like rocket science.
Danny Locher
I’ve used Filecoin for backup of personal photos and it’s been smooth; just remember to keep that seed phrase somewhere safe.
Donald Barrett
Exactly, and the formal audits give enterprises the compliance reports they desperately need.
Christina Norberto
Indeed, the highly formal nature of blockchain contracts provides an immutable record that satisfies many regulatory frameworks, though some argue it adds bureaucracy.
Chris Hayes
Your criticism of UI polish is fair, but the end user often cares more about reliability than visual flair.
Fiona Chow
Sarcasm aside, the tech stack does demand a learning curve, yet the security payoff justifies the effort.
Rebecca Stowe
Your optimism is refreshing; as more tools simplify the process, adoption will likely surge.
Alie Thompson
While I respect the enthusiasm expressed, it is crucial to acknowledge that decentralization does not automatically solve every security dilemma.
The systemic trust model shifts the burden onto users, who must now manage cryptographic keys with the same diligence traditionally handled by service providers.
In scenarios where keys are mishandled, the entire network’s promise of confidentiality collapses, rendering redundancy moot.
Furthermore, the incentive structures governing node participation can affect data durability, especially if economic rewards diminish.
It is also worth noting that network latency may impede real‑time applications, a factor often overlooked in enthusiastic discussions.
Therefore, a balanced assessment should weigh both the resilience benefits and the operational responsibilities imposed on end‑users.
Communities that foster robust key‑management education and transparent governance tend to mitigate many of these concerns.
Ultimately, embracing decentralized storage responsibly requires both technical safeguards and a cultural shift toward shared accountability.
Darren R.
Indeed; the points raised are compelling; nevertheless, vigilance remains paramount.
mark gray
Decentralization is the future.
Write a comment